Simplifying Security: Implementing Managed Identities for Secure Azure Resource Access

In an era where security is paramount, Azure provides a robust solution to safeguard resource access—Managed Identities. They introduce a mechanism for secret-less authentication and authorization, contrasting with the conventional practice of using Service Principals that require secret or specific keys to access Azure resources. This article offers an exploration of Managed Identities and provides a systematic approach to implementing them for secure Azure resource access.
The Fundamentals of Managed Identities
Managed identities enable Azure resources to authenticate to cloud services without storing credentials in code and are categorized into System-Assigned and User-Assigned.
System-Assigned Managed Identities are directly tied to an Azure resource. When the resource is deleted, so is its identity. It’s a one-to-one relationship. On the other hand, User-Assigned Managed Identities operate as separate Azure resources, meaning they can be associated with multiple Azure services. It’s the “reuse and recycle” principle in action, enhancing flexibility.
Azure Role-Based Access Control (RBAC) allows you to manage who has access to Azure resources, what areas they have access to, and what they can do with those resources. This is achieved by assigning roles to users, groups, or services, each role encapsulating a set of permissions.

When it comes to Managed Identities, Azure RBAC plays an instrumental role. With RBAC, you can specify precise permissions for a Managed Identity, determining what Azure resources it can access and what operations it can perform. It facilitates granular control over the access rights of a Managed Identity, thereby bolstering the overall security mechanism.
Azure.Identity and Azure SDKs
Azure.Identity is a key .NET library within the Azure SDK, that elegantly simplifies token acquisition from Azure Active Directory (AAD). It’s equipped with an array of credential classes, including Managed Identity credentials, aligning with diverse Azure AD authentication modes. A standout feature is its DefaultAzureCredential class, which leverages Managed Identities for authentication, streamlining the transition between development and production stages. This feature allows developers to write adaptable code that works seamlessly in both environments. The use of Azure.Identity enhances application security, scalability, and maintainability by abstracting sensitive authentication details.
Practical example integration
We want to show you how easy it is to leverage Managed Identities on Azure. Therefore, we created a new Azure Function and Managed Identity on Azure. Afterwards, the Managed Identity is assigned to the Azure Function via the Identity blade, as shown below.
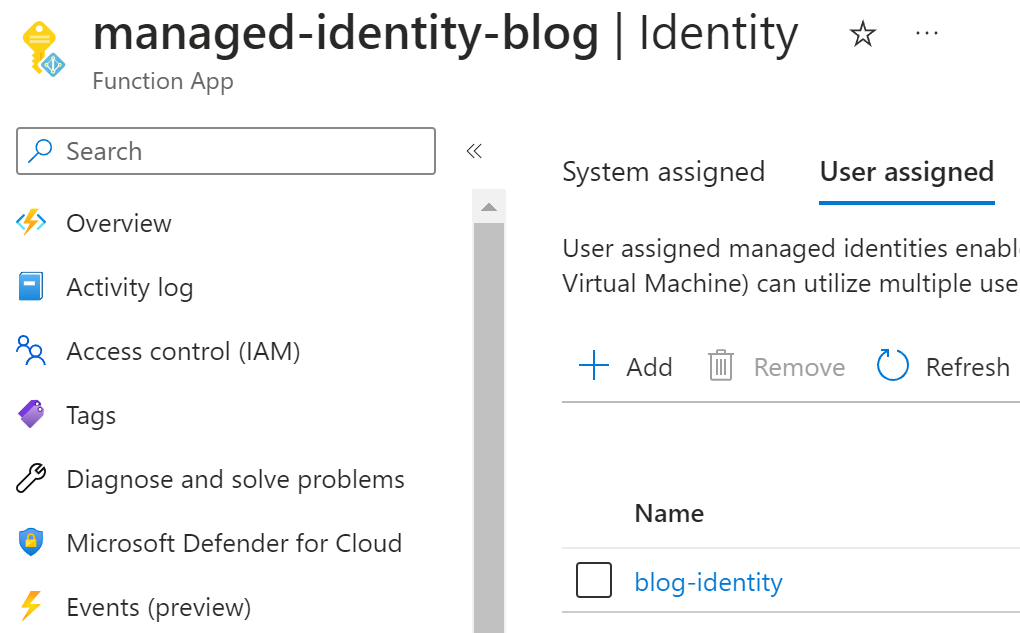
The Azure Function is now ready to use the assigned Managed Identity.
Example Integration with KeyVault
To familiarize you with the application of Managed Identities, let’s delve into an integration scenario with Azure KeyVault. As a prerequisite, you need to configure the permission for your Managed Identity via RBAC or an access policy, depending on your chosen permission mode on Key Vault.
For this scenario the NuGet package Azure.Security.KeyVault.Secrets and Azure.Identity are used, which allows simple integration using Managed Identities. The following code snippet shows how to create a client to access and fetch a secret from Key Vault:
1
2
3
var keyVaultUri = new Uri("myvault.vault.azure.net");
var secretClient = new SecretClient(keyVaultUri, new DefaultAzureCredential());
var secret = secretClient.GetSecret("my-secret");
Example Integration with Azure SQL and Entity Framework Core
Let’s consider Azure SQL in conjunction with Entity Framework Core Version 6 (and onwards). As a prerequisite, you need to grant the Managed Identity permission on your Azure SQL Database. This requires a couple of steps and configuration on your Azure SQL Server instance, which can be found here. For the sake of brevity, these steps are omitted in this blog post.
Going forward with Managed Identity, you just need to specify a connection string that looks like the one below:
"Server=demo.database.windows.net; Authentication=Active Directory Default; Encrypt=True; Database=testdb;"
The `Authentication` signifies your intention to utilize a Managed Identity-based connection to the SQL database. The following code snippet shows how to register a DbContext (from Entity Framework Core) using the identity-based connection string:
1
2
3
var dbConnectionString =
"Server=demo.database.windows.net; Authentication=Active Directory Default; Encrypt=True; Database=testdb";
services.AddDbContext<MyContext>(builder => builder.UseSqlServer(dbConnectionString));
Conclusion
This introduction offers a glimpse into the realm of Managed Identities and secure Azure resource access. For comprehensive insights into setting permissions for Managed Identities and other details, we highly recommend perusing the official Microsoft documentation.
Managed Identities are an invitation to refine your security strategy and direct your attention to what truly counts—crafting exceptional solutions. Stay connected for more insights, guidance, and tutorials on harnessing Azure’s prowess.
